Email addresses may seem unimportant, just a string with an “@”, but they can unlock a person’s digital footprint. Email OSINT uses open-source methods to gather details linked to an email address. It’s used in cybersecurity, fraud detection, journalism, and law enforcement to find useful clues about people or groups. In this article, we’ll explain what email OSINT is and why it matters. We’ll cover what you can discover, tools and techniques to use, plus limits and ethical concerns.
What Is Email OSINT?
Email OSINT (Open-Source Intelligence for email) is the process of gathering and analyzing publicly available data related to a target email address. The goal is to leverage that email as a starting point to find connected information across the web. By examining an email’s associations with social media accounts, online services, and data breaches, investigators can often identify the individual or organization behind the address and map out their online presence. In practice, email OSINT might involve anything from a simple Google search of the address to using specialized tools that check hundreds of websites for accounts tied to that email. This technique has become a crucial part of OSINT work because a single email can unlock a trove of intelligence revealing usernames, profiles, breach history, and other personal details that help build a comprehensive picture of the target.
Why Use Email OSINT?
Email OSINT provides significant value in various investigative and security contexts. Here are some real-world use cases that illustrate why this technique is so important:
Cybersecurity & Threat Intelligence:
Security analysts track threat actors by investigating suspicious email addresses used in phishing or cyberattacks. By analyzing an email’s background, they can assess if it’s linked to known malicious activity or determine the digital footprint of a potential attacker. For example, identifying social media or forum accounts tied to a hacker’s email might reveal their networks or past behavior, aiding incident response.
Fraud Detection & Anti-Abuse:
Businesses and fraud investigators use email OSINT to detect disposable or high-risk emails in user sign-ups. An email address that appears in spam blacklists or has no online history might indicate a throwaway account used for fraud. Checking an email against breach databases can also show if the user’s credentials were compromised, informing risk decisions. In short, it helps distinguish trustworthy users from likely scammers.
Criminal Investigations & Law Enforcement:
Law enforcement and private investigators leverage email OSINT to uncover the identity and activities of suspects. A single email could lead to social media profiles, aliases, or domain registrations that connect an unknown address to a real person. This is valuable in cases ranging from missing persons investigations to tracking down perpetrators of cybercrimes or harassment. It essentially turns an email into a starting clue for building an intelligence profile.
Journalism & Research:
Investigative journalists often use OSINT to verify sources or dig into persons of interest. An email provided by a source can be cross-checked for public profiles, forum posts, or leak mentions to gauge credibility. Journalists have also used email OSINT to expose connections (for instance, linking officials to secret accounts or uncovering that a seemingly anonymous tipster’s email is tied to certain organizations). It’s a non-intrusive way to follow the digital trail in research and fact-checking.
Penetration Testing & Social Engineering (Ethical Use):
Ethical hackers and red-teamers may perform email OSINT during recon. By finding a target’s associated accounts and personal details, they can craft more convincing phishing emails or test how exposed a company’s staff emails are. For example, discovering an executive’s email in a data breach along with a reused password can highlight a security weakness. (Of course, this is done with permission in professional security audits.)
In all these scenarios, the common theme is that an email address serves as a pivot to a wealth of open information. Properly utilized, email OSINT can validate identities, reveal hidden connections, and provide leads that would be hard to get otherwise all without requiring any illegal access.
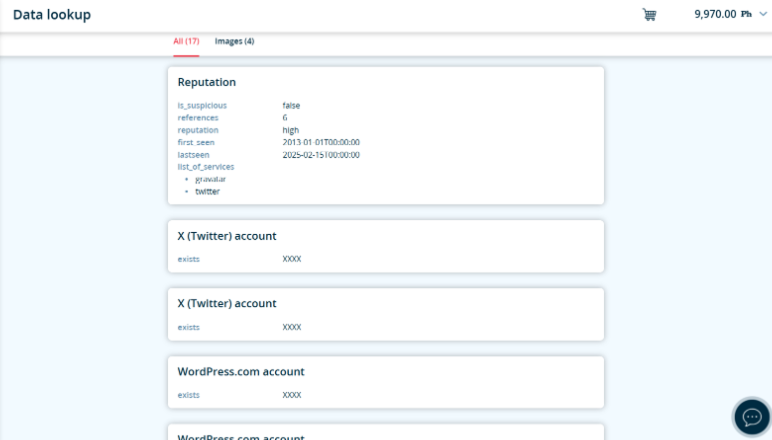
Information You Can Discover via Email OSINT
An email address can reveal a surprising amount of intelligence when examined with the right tools and techniques. Below are the key types of information investigators commonly uncover through email OSINT:
Basic Personal Details:
Often you can extract the owner’s name, approximate location, or even profile photos associated with an email address. People frequently reuse email addresses on social profiles or contact pages, so a simple search might turn up names in forum posts, online resumes, or social media pages. In some cases, the email’s username (the part before @) hints at the person’s name or nickname. Using Google with the email in quotes is a quick way to find any public mentions that contain those personal details.
Social Media Accounts and Usernames:
Email addresses are a common login identifier on social networks and other websites. By leveraging reverse email lookup techniques, investigators can find which platforms have user accounts tied to the email. For instance, a password reset form on Facebook or LinkedIn will indicate if an account exists with that email (sometimes even showing a partially masked name or phone number). In this way, a single email can lead you to discover profiles on social media, forums, gaming sites, or other online services that the person uses. These linked accounts help map out the target’s online identity and interests.
Social Media Content and Activity:
Beyond just finding the existence of accounts, email OSINT can reveal the content linked to those accounts if they’re public. Once you’ve identified, say, a Twitter or Instagram account via the email, you can examine the public posts, photos, interactions, and even check-ins for patterns. Investigators often find insights into a person’s lifestyle, interests, and social circle this way. Notably, many platforms (including some “niche” apps) allow searches by email in their people-finding features. If an individual used the same email for a fitness app like Strava or a travel site like Airbnb, those activities might surface too potentially revealing location trails or hobbies.
Associated Domains and Professional Info:
If the email is under a private or corporate domain (e.g. name@company.com), it opens up another avenue of inquiry. A WHOIS lookup on that domain can uncover registration details such as the domain owner’s name or organization, registration dates, and contact information (unless privacy protection is enabled). This is useful for tying the email to a business or employer. Additionally, you might find the email listed on company websites, press releases, or professional directories, which can tell you the person’s role or department. In essence, a custom-domain email often signals professional affiliation and can be used to gather corporate OSINT.
Data Breach Records:
One of the most valuable troves of information comes from data breach databases. By checking the email against known breach repositories (like the public site Have I Been Pwned), you can learn if the address was involved in any past data leaks. Breach data can expose associated usernames, passwords (usually hashed or redacted), and the services or websites where the email was used. For example, a hit might show that john.doe@example.com appeared in the LinkedIn breach, indicating John Doe had an account there. These findings help map out which services the person used, and also raise security flags e.g., if their information might be circulating on the dark web. Such intel is crucial for evaluating if an individual’s accounts are compromised or if they tend to reuse credentials.
Technical Traces (Email Headers and Servers)
If you have access to an actual email message from the target (or one they sent you), examining the email header can yield OSINT data too. Email headers contain metadata like the sending IP address, mail server info, and routing path. By analyzing a sender’s IP, you might geo-locate roughly where an email was sent from or which mail service was used. For instance, an email’s header could show it originated from a certain city or went through a specific SMTP server. This is particularly useful in fraud investigations or phishing analysis it helps determine if an email claiming to be from a company actually came from an unusual location or a known malicious server. These technical footprints add another layer of intelligence, helping verify if an email source is legitimate or part of a scam.
Each piece of information above can act as a pivot to find even more data. Email OSINT often becomes an iterative process: a social profile yields a photo that can be reverse-searched, a breach record gives a username that leads to other accounts, and so on. By assembling these puzzle pieces, investigators create a richer portrait of the person or entity behind the email.
Tools and Platforms for Email OSINT
Several email OSINT (Open Source Intelligence) tools available for investigating email addresses are actually free. Some popular options include HaveIBeenPwned, which checks if an email has been compromised in data breaches, and Epieos, which provides basic email address lookups. Other useful tools include Hunter.io for finding email addresses associated with websites and Mail-Tester.com for assessing email deliverability. Additionally, tools like Google Dorks, the Wayback Machine, and specialized search engines like Shodan and Censys can be helpful in gathering information related to an email address.
However when needing more in depth or complex functions you may find yourself needing one of the paid solutions such as Lampyre, VoilaNorber, ReverseGenie, Spokeo, Pipl etc. Each tool has its strengths, and often investigators will use them in combination. For instance, one might start with a quick HIBP breach check, then run Holehe for account discovery, and use SpiderFoot or an advanced platform for an in-depth dive. It’s also crucial to use updated tools (as website APIs and platforms change frequently) and ensure compliance with any usage policies or required API keys. New OSINT tools and services emerge regularly, so staying plugged into the OSINT community helps in keeping your toolkit current.
Techniques and Methodologies for Email OSINT Investigations
Conducting an email OSINT investigation typically involves a mix of manual techniques and automated methods. A structured approach ensures you cover the breadth of possible information. Below are some key techniques and methodologies, along with how they are applied:
Search Engine Queries (Google Dorking):
A fundamental first step is simply searching the email address on Google (or Bing, etc.) with quotes around it e.g., “target@example.com”. This query (often called a Google dork) forces the engine to return pages where that exact string appears. It can reveal forum postings, blog comments, public documents, or directory pages that mention the email. Investigators often try variations and additional keywords, like the email alongside a person’s name or with terms like “CV”, “profile”, “breach” etc., to narrow down context. Manual search is powerful because it can uncover unstructured tidbits that automated tools might miss such as a random blog where the person left a comment with their email, or a cached webpage listing contact emails. Always sift through several pages of results and use different engines if possible, since each may index slightly different content.
Social Media & Account Checks:
Another core method is to go directly to major platforms and see if the email can be used to find a user profile. Some social networks allow searching by email in their people search or during account recovery. For example, plugging an email into Facebook’s “Forgot Password” form will show if an account exists and often partially reveal the profile name or picture.
Similarly, LinkedIn’s contact import or Twitter’s reset link can indicate an associated user. OSINT investigators use these features carefully: the idea is to confirm account existence and harvest any clues (like usernames or profile images) without logging in or triggering alerts. On platforms that don’t allow direct email lookup, one trick is to search the email within the platform via its search bar (some forums or smaller sites might index emails publicly in user profiles). Overall, by manually checking a handful of popular sites social networks, e-commerce, gaming sites you can often get hits that then lead you to the person’s profile pages.
Email Header and Domain Analysis:
If you possess a sample email (for instance, the target emailed you or you found a leaked email file), examining the email header can yield investigative clues. Viewing the full header (in Gmail, Outlook, etc., there’s an option to view “original” or “message source”) exposes metadata including the sender’s IP address, the mail server used (SMTP relay), authentication results, and timestamps. From the header, you might find the originating IP, which can be run through a WHOIS or IP geo-location lookup to get a rough location or internet service provider.
You can also see the path an email took sometimes highlighting an unexpected server (e.g., a personal email sent from a corporate mail server might indicate misuse). Additionally, the domain of the email itself (after the @) should be checked: performing a WHOIS lookup on the domain can provide registrant details if not private. You might discover that a seemingly generic email (like name@randomdomain.com) is actually tied to a small business or a specific person via WHOIS. This technical sleuthing is especially useful in fraud and phishing cases, where confirming the source of an email is critical.
Breach and Leak Searches:
To explore historical data, investigators search the email in breach databases and paste sites. Manually, you can use sites like Have I Been Pwned to see a list of known breaches. For deeper searches, platforms like DeHashed or Scylla let you query many breach sets and pastes. Some of these may need a login or API key. The goal is to check if the email appears in leaked credentials or on dump sites like Pastebin. If found, records might show usernames, hashed passwords, or other details used across different sites. This can enrich the profile, revealing usernames to search in other places.
It’s important to handle any leaked data ethically and legally. Use public breach services or data you have permission to access. From an OSINT view, breach data can confirm links between an email and specific websites. It can also reveal old accounts the person may have forgotten.
Automation with OSINT Tools:
After targeted manual checks, analysts often use OSINT tools to expand the search. These tools can query many platforms and databases at once. For example, running an email through SpiderFoot or a similar tool activates several modules in one go. It checks social networks, public APIs, search engine results, and scans for related usernames, then combines the results. This process can reveal hidden details, like an account on a small website or a mention in old news. These are things that manual checks might have missed.
Automated tools save time on repeated checks, like testing one email across 100+ sites using Holehe. The key method is to configure the tool carefully, add needed API keys, select modules, and let it run. The results often need review and verification since tools can show false positives or incomplete data. Still, when used well, automation finds leads a single investigator might miss or not have time to discover. It’s a force multiplier in email OSINT, especially for those who need fast and thorough results.
Documentation and Pivoting:
A key OSINT method is documenting each finding and using it to pivot to the next discovery. For example, if you find a social profile, record the username and URL. Then, search the username separatelyit might be reused on other platforms. If you find a profile picture, do a reverse image search to see where else it appears. If a phone number or address appears, search those details too. Taking good notes helps you catch more pivot points. Many investigators use spreadsheets or special tools to log each piece of info found. They also record where the information came from. By the end, you build a chain of evidence from the first email to everything connected to it.
By combining methods from basic Google dorking to advanced automation, an email OSINT investigation becomes more systematic and thorough. It’s often an iterative cycle where manual steps guide automated searches and automated results inform manual follow-ups. The investigator’s intuition and experience help decide which technique to try next based on the clues found so far.
Conclusion
Email OSINT can turn one email address into a rich trail of online clues. Whether you work in cybersecurity or journalism it’s useful to link an email to real identities or online behavior. But it’s also important to use these methods responsibly and know their limits. Not all data is available, and not every lead is reliable on its own.
If you’re exploring tools to support deeper investigations, Lampyre is one option worth checking out. It offers advanced features for email OSINT alongside broader capabilities in data analysis and visualization. While it might not be necessary for basic lookups, it can help when your investigations require more depth or scale.
The key is to match the tool to the taskand always document your findings carefully. OSINT is as much about how you use the information as what you uncover.
Sources:
- Hackers-Arise – The Versatile Email Address (Mosint tool features) hackers-arise.com.
- Medium (Melusi Shoko) – Email OSINT (EmailRep use cases) osintteam.blog.
- UserSearch Blog – Top OSINT Tools for Email Addresses (2024) usersearch.org.
- OSINT Combine – Investigating Email Addresses (OPSEC concerns) osintcombine.com.
