Free OSINT Tools: 10 Best Options to Start Open Source Intelligence Open source intelligence (OSINT) means collecting information from public places on the internet. That includes websites, social media, public records and archived pages. OSINT helps journalists, security teams, researchers, and curious people learn more about a person, company or event. You do not need an expensive subscription to begin. Many tools are completely free and useful for general tasks. This article lists ten free OSINT tools, explains what they do, and shows how to use them together. How to Pick a Free OSINT Tool Free does not always mean simple. When you choose a tool, check: What it finds. Some tools look for usernames. Others map networks or extract image metadata. How you use it. Some tools run in a web browser. Others need the command line. Limits. Free tools may have rate limits or fewer features than paid ones. Support. Active projects with documentation and community help are easier to use. Also keep legal and ethical rules in mind. Public data can still be sensitive. Do not break terms of service or privacy laws. Top 10 Completely Free OSINT Tools Below are the ten tools we recommend. Each entry has a short use case, main strengths, platform and a source note you can link to from your site. 1. Maltego (Community Edition) Summary Maltego is a visual link analysis tool that maps relationships between domains, IPs, emails and accounts. It uses “transforms” to fetch and connect data. The free Community Edition has limited results per transform but remains useful for visualization. Use case Mapping the digital footprint of a company or showing how multiple domains link together. Pros Clear visual graphs. Many built-in transforms. Exports in multiple formats. Cons Limits in the free edition. Learning curve for new users. 2. SpiderFoot (Community Edition) Summary SpiderFoot automates reconnaissance by scanning hundreds of sources for data on domains, IPs, emails and more. It can run locally with a web UI or from the command line. Use case Running a broad scan on a domain to find subdomains, breaches, and linked accounts. Pros Very broad coverage of sources. Automated scans save time. Reports export to JSON, CSV, HTML. Cons Some modules need API keys. Large scans produce overwhelming data. 3. Recon-ng Summary Recon-ng is a command-line framework for web-based reconnaissance. It organizes modules for tasks like WHOIS lookups, DNS queries and social media checks. Results are stored in a built-in database. Use case Automating domain reconnaissance during a security assessment. Pros Modular and customizable. Built-in data storage and reporting. Good for automation. Cons CLI only, not beginner-friendly. Requires API keys for many modules. 4. theHarvester Summary theHarvester gathers emails, names, subdomains and IPs from public search engines and other data sources. It is simple, fast, and widely used in the first stage of recon. Use case Collecting email addresses and subdomains tied to a company. Pros Lightweight and easy to run. Works with multiple search engines. Good starting point for domain OSINT. Cons Limited scope (only basic identifiers). No advanced analysis or visualization. 5. Shodan (Free account) Summary Shodan is a search engine for internet-connected devices. It indexes banners, open ports, and metadata from exposed systems worldwide. A free account allows limited queries. Use case Finding exposed webcams or servers running outdated software. Pros Huge database of internet devices. Filters for ports, country, and product. Simple web UI. Cons Free tier has strict query limits. Some advanced filters are paid. 6. Censys Summary Censys is another search engine for internet-facing hosts and TLS certificates. It scans the global IPv4 and IPv6 space and provides structured query results. Use case Discovering all certificates tied to a company’s domain. Pros Detailed host and certificate data. Strong query language. Active research community. Cons Free accounts limited in daily queries. Query syntax can be complex for new users. 7. OSINT Framework Summary OSINT Framework is a curated web directory of OSINT tools and resources. It organizes links by task (usernames, images, public records, etc.). Use case Finding the right tool when you don’t know where to start. Pros Huge range of categorized tools. Easy to browse. Regularly updated. Cons It only points to tools, does not gather data. Some links may break over time. 8. Wayback Machine (Internet Archive) Summary The Wayback Machine archives billions of webpages. It lets you view snapshots of a site from past dates, useful for recovering deleted or changed content. Use case Checking what a company website looked like before content was removed. Pros Free and easy to use. Large historical archive. API available for automation. Cons Not every site is archived. Some pages may be incomplete. 9. FOCA (Metadata extraction) Summary FOCA scans domains for public files (PDFs, Word docs, etc.) and extracts hidden metadata such as usernames, software versions, and paths. Use case Discovering employee names and internal details hidden in metadata of public documents. Pros Bulk metadata extraction. Supports many file types. GUI for easier use (Windows). Cons Less maintained today. Works only if files with metadata are accessible. 10. Sherlock Summary Sherlock is a Python tool that checks hundreds of websites for a username. It reports where a handle is registered. Use case Finding a person’s accounts across social media and forums. Pros Large, community-maintained site list. Fast and parallel scanning. Easy to extend with new sites. Cons Only checks existence, not identity. Some sites may block queries. Simple Workflow Using These Free Tools No single tool finds everything. Here is a short workflow you can follow when you start a new OSINT task. Define scope. Decide if you are looking at a person, domain, or device. Write one clear question. Start with directories. Use the OSINT Framework to pick tools for the task. Find identifiers. Run Sherlock and theHarvester to find usernames, emails, and subdomains. Gather broader data. Feed those identifiers into SpiderFoot or Recon-ng to expand discovery. Inspect infrastructure. Use Shodan or Censys to check for exposed devices or open ports. Extract file
How to Find Connections Between Companies and People Using Lampyre: A Due Diligence Tutorial
When doing due diligence, it’s important to uncover how companies and people may be linked. These connections can reveal potential risks, hidden partnerships, or opportunities that aren’t visible at first glance. In this tutorial, we’ll walk through how to use Lampyre to search for ties between organizations and individuals. You’ll learn the basic steps, what kind of data can be uncovered, and how to interpret the results so you can make more informed decisions. In this tutorial, we will learn how to search for connections between companies and people using Lampyre. To begin, open the Lampyre application and create a new project file. Starting with a fresh file helps keep your investigation organized and ensures that the results you gather are stored in one place. Step-by-Step Guide: Finding Company and People Connections Step 1: Open the Scheme Tab First, we will open the Scheme tab, which can be found under “File” in the navigation menu at the top. This is where you’ll build your investigation visually. Step 2: Add a Company to the Canvas In the Presets section, locate “British company” and drag it onto the canvas. This will open the Properties tab, where you can enter the company’s information such as the company number or name. Step 3: Send Your First Request Now that this step is complete, we can send our request. To do this, right-click on the element in the canvas. A list of available requests will appear, based on the information you entered earlier. In our case, we will send two requests using the company number. Step 4: View Your Results In the left bar, you will be able to track your requests loading. After they are completed, you will be presented with a connection graph in your main canvas. If you would prefer a table view, just double-click on the request for a different view. Step 5: Expand Your Search to Find More Companies Since we were able to find all legal persons connected to this company number, we can now expand our search to see every company those people are linked to. To do this, go to the Content tab in the bottom-right corner, select People, right-click, and start another request (as shown in the picture below). Step 6: Organize Your Results with Hierarchical View And just like that, we are presented with every possible company connection. If you want to organize the results, navigate to the icon menu on the left and select Hierarchical View, or press Ctrl+6 to sort your connections into a clearer structure. As before, you can also double-click on the request to open it in a new table view. Step 7: Explore Connections and Use the GIS Map Now, let’s explore the connections between two points. To do this, take the table and drag it, which will open the Position menu. For example, you can place it below the Schema. When you select a person in the table, that same person will also be highlighted in the Schema. This makes it easier to organize your connections. You can also select individual items and resize or move them to make certain elements stand out. If you’d like to go a step further, you can open the GIS Map. This will display the same elements on an actual map, allowing you to see where those people are working from. Final Thoughts With these steps, you now have the basics of using Lampyre for due diligence. By starting with a single company number, we were able to uncover the people connected to it, map out their ties to other companies, and even visualize those links on a GIS map. This workflow shows how Lampyre can help transform scattered data into a clear picture of relationships between organizations and individuals. From here, you can continue refining your searches, exploring new requests, and building a deeper understanding of the networks you’re investigating. Start with one connection and let the data guide you to the bigger picture.
OSINT Framework: A Beginner’s Guide to Open-Source Intelligence
This article was updated and actualized with new data on November 18, 2025. OSINT framework is a structured way to collect and analyze information that is publicly available online. Social media posts, blogs, public records, and even leaked databases can all reveal valuable insights about people, businesses, and events. With the right approach, this data turns from noise into intelligence. This process is known as open-source intelligence, or OSINT. OSINT started as a military and government activity. Agencies collected information from newspapers, radio, and later the internet. Over time, it expanded into fields like cybersecurity, journalism, corporate risk management, and even personal research. A journalist might use OSINT to verify a politician’s statements. A company might screen potential partners. A cybersecurity analyst might track suspicious domains. But there’s a challenge: the internet is massive. Without structure, searching can feel like finding a needle in a haystack. That’s why OSINT frameworks exist. They provide a roadmap, guiding you from one data source to the next. For beginners, a framework removes guesswork. For professionals, it makes investigations faster and more reliable. In this article, we’ll explore what an OSINT framework is, why it matters, examples of popular frameworks, and how to use them effectively. We’ll also cover the benefits and limitations of frameworks and show how they connect with professional OSINT tools like Lampyre. What Is an OSINT Framework? An OSINT framework is a structured collection of tools, methods, and categories designed to help you gather information systematically. Think of it like a toolbox with labels. Instead of one big pile of wrenches and screwdrivers, each drawer is labeled: “emails,” “domains,” “social media,” “phone numbers,” and so on. When you need to investigate an email address, you open the “emails” drawer and see a list of tools that can help. Frameworks usually exist as either: The key idea is consistency. You don’t reinvent the wheel for every search. You follow a logical sequence, ensuring you don’t overlook valuable sources. Framework vs. Tool vs. Method It’s easy to confuse these terms, but they’re not the same: Without a framework, beginners can get lost in endless tool lists. With one, the process feels more like following a map. Why Use an OSINT Framework? The value of frameworks becomes clear once you try doing OSINT without one. Imagine investigating a username. Where do you start? Do you search Google, check Twitter, or look at niche platforms? Without structure, you waste time repeating searches or overlooking key sites. Frameworks solve this by: A Beginner Example Suppose you’re curious about a username you saw online. Using a framework, you’d: This flow saves you from randomly searching Google over and over. A Professional Example Law enforcement might use a framework to investigate a phishing campaign. Starting with the malicious domain, the framework points them to: Each step builds on the previous one, creating a full picture. Popular OSINT Frameworks You Should Know 1. OSINT Framework (by Justin Nordine) This is the most widely recognized framework. It’s a web-based tree of OSINT categories. You start with a data type like an email address and click through branches leading to related tools. For example, under “Email Addresses,” you might find links to tools for breach checks, validation, or social media lookups. 2. Maltego CaseFile Maltego is known as a professional OSINT platform, but it also has CaseFile, a free framework for visual link analysis. Instead of clicking through lists, you create a map of entities like people, emails, and companies. This visual style makes it easier to see relationships. For instance, a single email might connect to several domains, which link to different IP addresses. 3. IntelTechniques Framework Michael Bazzell’s IntelTechniques site provides a structured set of resources, especially focused on people searches. His guides and workbooks are often used by investigators in both government and private sectors. 4. Sector-Specific Guides Different industries adapt frameworks to their needs: These frameworks may not be as polished as OSINT Framework, but they show how adaptable the concept is. How to Use an OSINT Framework: Step-by-Step Guide Let’s walk through a practical example using a suspicious email address: The framework ensures you don’t stop at step 2. It nudges you to explore connected data points. For bigger investigations like tracking a phishing campaign or analyzing disinformation, teams can assign different branches of the framework to different people. That way, nothing slips through the cracks. Benefits and Limitations of OSINT Frameworks Benefits Limitations Frameworks are excellent starting points. But when the stakes are high—say, for law enforcement or corporate security—they can feel limited. That’s when professionals move toward automated platforms. Free Tools Commonly Found in OSINT Frameworks Frameworks often list dozens of free resources. Here are a few well-known ones: Each tool solves a small piece of the puzzle. Frameworks help you connect them into a workflow. OSINT Frameworks and Professional Tools Frameworks are useful, but they’re static maps. They point you to where data might be but don’t collect it for you. Professionals often need more: Lampyre: The Next Step Beyond Frameworks This is where professional tools like Lampyre come in. Lampyre offers a desktop and web application that integrates 100+ data sources with 60+ input types into a single environment. Instead of manually jumping between tools, you run automated checks and see connections in one place. Key advantages of Lampyre over manual frameworks: For beginners, frameworks are a great entry point. For professionals or organizations, solutions like Lampyre make OSINT faster, deeper, and more reliable. Conclusion: Choosing the Right OSINT Approach An OSINT framework is like a roadmap for online investigations. It organizes the chaos of the internet into a logical workflow. Beginners can use frameworks to learn the basics, while professionals can build on them for larger investigations. Popular frameworks like OSINT Framework, Maltego CaseFile, and IntelTechniques offer great starting points. They teach you how to move from one clue to the next without losing focus. Still, frameworks have limits. They’re free and accessible, but they don’t automate or visualize
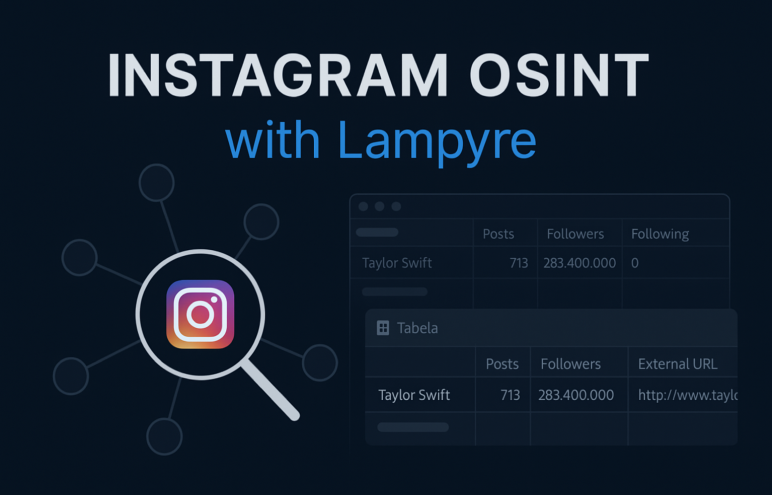
How to Research Instagram Profiles with Lampyre: An Instagram OSINT Tutorial
Instagram is one of the most popular social media platforms in the world, with millions of users sharing photos, videos and stories every day. Its massive user base makes it a valuable resource for Instagram OSINT, where investigators, researchers, and analysts use publicly available data to gain insights. Public profiles, posts, and interactions can reveal useful information about people, organizations, and online communities. Lampyre simplifies this process by collecting and analyzing Instagram data in one place. In this tutorial you’ll learn how to use Lampyre to research Instagram accounts, uncover connections, and identify patterns that might not be visible at first glance. In this article we’ll show you how you can start investigating Instagram accounts using Lampyre’s OSINT capabilities. But before we dive in, let’s first answer the question: What is Instagram OSINT? What is Instagram OSINT? Instagram OSINT refers to the practice of collecting and analyzing publicly available data from Instagram to gain insights into people, groups, or events. OSINT stands for “Open-Source Intelligence,” which means the information is gathered from sources that are openly accessible on the internet, not from private or hacked accounts. On Instagram, this data can include profile details, posts, hashtags, comments, likes, tagged accounts, and even geolocation information if it is made public. Investigators, journalists, researchers, and businesses use Instagram OSINT to track trends, verify identities, uncover networks, or study online communities. Because Instagram is built around visuals and social interactions, it often reveals connections and behavioral patterns that may not be obvious at first glance. Using OSINT tools helps streamline the process by automating searches, mapping relationships, and organizing the results in one place. This makes Instagram OSINT more efficient and reduces the time needed to dig through large amounts of content manually. How to Use Lampyre for Instagram Research First, open the Lampyre app and start a new project. Once the project loads, you will be redirected to the dashboard, where you can navigate to Windows and select List of Requests, or use the shortcut Ctrl + Y. In the list view you can search either by Criteria or by Tasks. Simply type in Instagram, and Lampyre will display all Instagram-related tasks that you can run. For the purposes of this tutorial, we will be checking a celebrity’s Instagram account. As an example, locate the option “Instagram account info by account username or ID.” This request will fetch all available extended information on an Instagram account by its ID or username (or even a list of IDs or usernames). Note that this request does not provide geolocation data or details about users tagged in the posts of the account. To demonstrate, let’s use Taylor Swift’s Instagram account. Simply enter her username into the request and wait for the Lampyre app to crawl her profile. After a short wait, Lampyre will display the basic information about the profile along with any hyperlinks from the bio, which you can click directly within the app. The results are shown in two main tabs: one for profile information and another for profile statistics, such as follower count, number of posts, and tags. In some cases, users also have their contact information linked to their profile, which can provide even more insights for your investigation. Now let’s return to our data. On the right side of the navigation panel, you can change the way the results are displayed by going to Schema, selecting all elements, and clicking Run. This will generate a new, graph-like view of the data. To dig deeper into Taylor Swift’s account, right-click on her profile in the graph, which will open a new window with additional options. From here, you can use the Request window at the bottom, type in Instagram, select “Instagram post info…”, and then click Run to gather more detailed information about her posts. After running the request, Lampyre will display a much larger set of information about the account’s posts. This includes details such as who was tagged, who collaborated on the posts, which posts gained the most attention, and when and where they were published. On the right-hand table, you can also sort the data in different ways, such as by the number of likes or comments. Returning to the graph view, there is another powerful Instagram OSINT feature: if the account has tagged friends in their posts, you can locate those profiles on the graph, right-click on them, and run a search within the same graph. This allows you to expand your Instagram profile analysis and uncover connections that might otherwise be missed. You can also use Lampyre’s geolocation feature to check whether a person has used any geo tags in their Instagram posts. If available, this data will show you where the posts were made, adding another layer of insight to your Instagram OSINT investigation. Now let’s turn to the Instagram Recognize Objects in Photo table, which can be found in the folder panel on the left. By opening it, you will see a table view that lists details about the images in the account. For example, you can quickly check how many posts contain cats, shoes, or other recognizable objects. This feature is especially useful for Instagram OSINT because it helps identify patterns and recurring themes in a user’s visual content. Conclusion The examples in this tutorial only scratch the surface of what you can achieve with Lampyre when performing Instagram OSINT. From gathering basic profile information to analyzing posts, exploring tagged connections, reviewing geolocation data, and even detecting objects in photos, Lampyre makes it possible to uncover insights that would be difficult to find manually. Whether you are an investigator, researcher, or simply someone interested in understanding online behavior, Instagram OSINT can reveal valuable patterns and relationships. With Lampyre, all of this data is collected and visualized in one place, giving you the ability to move from raw information to actionable intelligence much faster. If you are ready to explore deeper connections and conduct your own Instagram profile analysis, download Lampyre and try
Discover a Powerful Epieos Alternative with Lampyre
Email lookup tools play an important role in open-source intelligence (OSINT). They allow investigators to connect an email address with online accounts, social media profiles, and activity timelines. Epieos is one of the better-known options in this space, widely used for its ability to reveal Gmail account activity and linked services. In the sections below, we’ll look at how Epieos works, what it offers, and then compare it with our OSINT tool, to see why Lampyre is considered as the best Epieos alternative. What is Epieos? Epieos is an OSINT tool that specializes in email-based investigations. By entering an email address, users can retrieve connected accounts, social media profiles, profile pictures, and sometimes phone numbers or usernames. Its services are mainly geared toward quick checks for journalists, security researchers, or individuals wanting to verify online identities. Epieos Key Features: While Epieos is convenient for email OSINT, it lacks advanced visualization, large-scale automation, and the broader data sources that professionals often require. What is Lampyre? Lampyre is a complete OSINT and data analysis platform that lets you investigate not only emails but also phone numbers, domains, IPs, usernames, vehicles, companies, and much more. It supports both desktop and web apps, with optional API integration for enterprise workflows. Lampyre Key Features: Lampyre vs Epieos: Pricing & Plans plans Lampyre Epieos Trial $5.00 trial Free limited tier Basic Plan $116.00 / month €3.50 per month (premium email lookup) Enterprise Custom pricing Not offered Why Choose Lampyre as an Epieos Alternative 1. Broader OSINT Capabilities Epieos is designed mainly for email lookups, which makes it very useful when the investigation begins with an email address. It can uncover connected accounts and provide Gmail activity details. However, many investigations require more than just email analysis. Lampyre covers a much wider set of selectors, including: This broader scope makes Lampyre a tool that can be used across different types of OSINT cases, not just those that start with email. 2. Visualization and Workflow Automation With Epieos, results are presented in a simple text-based format. While straightforward, it can be limiting when working with larger datasets or when trying to see connections between multiple entities. Lampyre, in contrast, supports: For teams working on complex cases, visualization and automation can reduce time spent on manual checks and improve the clarity of results. 3. Enterprise-Grade Security and Flexibility Epieos operates as a cloud-only service with limited customization options. This makes it convenient for quick checks but less suited for environments with stricter data handling requirements. Lampyre provides additional flexibility, including: This flexibility gives organizations more control over how they deploy and integrate OSINT tools into their workflows. Lampyre vs Epieos: Feature Comparison Feature Lampyre Epieos Email Lookup ✅ Yes ✅ Yes Phone/Username Lookup ✅ Yes ❌ No Graph-Based Visualization ✅ Yes ❌ No Bulk Data Import/Export ✅ Yes ❌ No Cloud/On-Premise ✅ Both Cloud only API & Custom Integrations ✅ Yes ❌ No Data Sources 100+ Limited (email-focused) Is Lampyre the Right Epieos Alternative? If you only need quick, one-off email checks, Epieos may be enough. But if you’re working in cybersecurity, OSINT investigations, fraud detection, or law enforcement, you need more than a single-function tool. Lampyre gives you: Switch to Lampyre as your Epieos Alternative Today Go beyond simple email lookups. Lampyre offers the scalability, data depth, and visual power needed for professional investigations. 🚀 Start your trial today and see why analysts worldwide trust Lampyre for their OSINT workflows. This post is an informational comparison only. All trademarks are the property of their respective owners. Specs, prices, and features can change at any time. If you spot an error or want to suggest an edit, shoot a note to feedback@lampyre.io.
Discover a Powerful Spokeo Alternative with Lampyre
When it comes to finding information on people, most internet users are familiar with services like Spokeo – a people search engine that aggregates public records into easy-to-read reports. But there are also powerful Open Source Intelligence (OSINT) tools like Lampyre that can serve as alternatives to Spokeo. Lampyre isn’t as widely known among casual users, yet it offers broad data-gathering capabilities and analytical features. This article will explain what both Spokeo and Lampyre are, and compare their features, pricing, and use cases in simple terms. Whether you’re an OSINT enthusiast or just someone starting out looking for people-search solutions, this comparison will help you understand how Lampyre stacks up as a Spokeo alternative. What is Spokeo? Spokeo is an online people search platform designed to find details about individuals using public data. It allows you to look up a person by entering a piece of information such as their name, email address, phone number, or mailing address. Spokeo then scours billions of public records – including phone directories, social media, property deeds, court records, and more – and compiles the results into an accessible report. One of Spokeo’s strengths is its ease of use. You simply input one piece of information and Spokeo “handles the rest” by automatically aggregating data from its vast databases. The service has become quite popular in the United States, reportedly serving about 23 million users per month and processing roughly 500,000 searches a day. However, Spokeo’s comprehensive results apply only to individuals in the United States (or U.S. citizens). On the financial side, Spokeo is a paid service (after a tiny teaser). It offers a 7-day trial for $0.95, after which a subscription is required. The pricing plans are subscription-based and relatively straightforward: a one-month membership costs about $19.95, or you can opt for a three-month plan which works out to $14.95 per month (billed as $44.85 every three months). For more demanding needs, Spokeo also has a Professional plan at $69.95 per month that permits up to 500 searches monthly. What is Lampyre? Lampyre is a multifaceted OSINT tool designed for data analysis, visualization, and investigation across a wide range of sources. Unlike Spokeo, which is a single website for people lookup, Lampyre is a software platform (available as a desktop application and also via web interface/API) that can collect and correlate information from over a hundred different data sources. Users can start an inquiry with just one data point – for example, a person’s name, an email address, a phone number, or even technical identifiers like an IP address or a domain name – and Lampyre will sift through its many sources to retrieve relevant information. The tool then let’s you organize and examine the results in various formats: you can view findings in tables, plot them on maps, or visualize connections on graphs. Lampyre vs Spokeo: Pricing Breakdown Plan / Feature Lampyre Spokeo Trial $5.00 (30 photons, 1 month trial) $0.95 (7-day trial) Basic / Lite Plan $8.00/month (100 photons) $19.95/month (100 searches) Mid Tier $77.00/month (1000 photons) $14.95/month billed quarterly ($44.85 every 3 months) Top Tier / Pro $116/month (PLUS plan, 1000 photons) $69.95/month (500 searches, Professional plan) Pay-as-you-go Option ✅ Available via Photons (credit-based) ❌ Not available Query Overages Buy additional credits (Photons) Must upgrade to higher plan International Data Access ✅ Yes (global sources) ❌ U.S. only Offline Use ✅ Yes (desktop version) ❌ No (web-based only) Feature Comparison Feature Lampyre Spokeo People Lookup ✅ Yes ✅ Yes Email/Phone/Name Search ✅ Yes ✅ Yes Global Data Sources ✅ Yes ❌ U.S. only OSINT Capabilities ✅ Extensive ❌ Basic Data Visualization ✅ Graphs, maps, tables ❌ None API Access ✅ Yes ❌ No Social Media Monitoring ✅ Yes ❌ No Data Import / Export ✅ Yes ❌ Limited Key Differences Between Spokeo and Lampyre Data Coverage & Sources: Spokeo focuses on aggregating public records and personal data mainly within the U.S. Lampyre draws from over 100 data sources globally, including technical and open web sources. Ease of Use: Spokeo is plug-and-play with instant results. Lampyre offers deeper functionality and analysis tools, which may require a learning curve. Results and Analysis: Spokeo gives pre-packaged reports. Lampyre enables deep dives, pivoting between data points, and visualizing connections. Geographic Focus: Spokeo is limited to U.S. records. Lampyre works globally. Pricing Model: Spokeo uses fixed subscription plans. Lampyre offers flexible credit-based pricing with scalable options. Privacy and Data Control: Lampyre allows offline use and user-defined data sources. Spokeo is fully cloud-based. Reasons to Choose Lampyre as a Spokeo Alternative Broader OSINT Capabilities: Lampyre can perform social media analysis, breach checks, and dark web queries, far beyond Spokeo’s people search. Flexible and Potentially Cheaper Pricing: You can spend just a few dollars with Lampyre if you’re a light user. It’s scalable and avoids the flat-rate model. In-Depth Analysis and Customization: Lampyre let’s you visualize relationships and build complex investigations. Spokeo is more of a one-and-done report. International and Niche Searches: If your investigation includes non-U.S. entities or specialized targets (like domains, IPs, crypto), Lampyre is the better fit. Combining with OSINT Workflows: Lampyre integrates well into analyst workflows with export options, graphing, and scripting. Conclusion Spokeo is best for users who need a fast, straightforward people lookup tool focused on U.S. public records. Lampyre is a powerful alternative for those who want global access, deep-dive investigations, and flexible pricing. While Spokeo is easier to use, Lampyre gives you far more room to grow and dig deeper. Choose based on your needs, how much control you want over the investigation process, and your comfort level with using more advanced tools.
OSINT Username: Investigate Online Identities Effectively
OSINT username searches turn online handles into investigative leads. A single username can connect an individual or organization to profiles, posts, and activities across multiple platforms — from social media and forums to online marketplaces. For analysts, journalists, and security teams, investigating usernames is a way to uncover relationships, verify identities, and trace digital activity. It’s about more than finding where a name appears; it’s about linking patterns, cross-referencing other identifiers like emails or phone numbers, and building a clear picture from scattered public data. In this guide, we’ll explain how username OSINT works, why it matters, and the tools that can help make the process faster, deeper, and more accurate. What is OSINT Username Search? An OSINT username search is the process of investigating a specific username or handle to discover where it appears online and what information is linked to it. The term “OSINT” stands for Open-Source Intelligence, which means the data comes from publicly accessible sources rather than from private databases or hacking. When someone uses the same or similar username on multiple platforms, those accounts can be connected to create a fuller picture of their online presence. Even small details, like profile pictures, posting habits, or writing style, can help confirm whether accounts belong to the same person. This kind of search is useful because usernames often stay consistent over time. While people might change their email address or phone number, many keep the same handle for years, especially on hobby forums, gaming platforms, or social media. That consistency makes usernames a strong starting point for investigation. However, the process goes beyond typing a name into a search engine. Analysts often check dozens or even hundreds of websites and platforms to see where a username appears. They might then cross-reference the results with breach data, domain registrations, or archived pages to find connections that aren’t immediately obvious. Used correctly, OSINT username searches can uncover valuable insights for cybersecurity teams, law enforcement, journalists, and businesses. But they also require careful verification to avoid false matches, since popular usernames may belong to different people on different sites. Why Username OSINT is Important Investigating usernames might sound simple, but it can have a major impact in fields where accurate identification matters. For cybersecurity teams, tracking a username across platforms can be the first step in uncovering a phishing campaign or detecting an impersonation attempt. If a threat actor is posing as a company representative, finding other accounts linked to that same username can help security teams take action before damage is done. In fraud investigations, usernames often act as threads that connect seemingly unrelated activities. A scammer who uses the same handle to advertise fake products on one site might also use it to communicate with victims on another. By following that trail, investigators can map the scope of fraudulent activity and sometimes identify the person behind it. Journalists and researchers also rely on username OSINT to verify information and confirm the credibility of their sources. In high-stakes reporting, being able to link a username to a history of posts, comments, or other accounts can help confirm whether someone’s claims are legitimate. Businesses use these techniques for brand protection and due diligence. If an unknown profile is using a company’s name or logo, an OSINT search can help determine whether it’s an authorized account or a potential impersonator. Similarly, before entering into a partnership, a company might investigate a potential partner’s usernames to see if they’re connected to controversial or fraudulent activities. In each of these cases, the value lies in connecting pieces of public information into a clear, reliable picture. A single username can open the door to a much larger investigation, and the insights gained can inform decisions that prevent financial loss, reputational damage, or security breaches. How OSINT Username Search Works A username investigation usually begins with a single piece of information — the handle you want to research. From there, the goal is to find every place that username appears online and understand how those appearances connect. This process involves more than just typing the name into a search bar. Skilled investigators use a combination of tools, techniques, and verification steps to get reliable results. The first step is platform scanning. Specialized OSINT tools can check hundreds of websites, social media platforms, and forums to see if the username exists. These scans can reveal obvious matches, like a Twitter or Reddit profile, but they can also uncover less obvious results, such as accounts on niche hobby forums or regional marketplaces. Next comes cross-referencing. A username on its own might not be enough to confirm identity. Analysts look for other clues — like profile pictures, bio details, or linked websites — to determine whether two accounts belong to the same person. If the username appears in breach data, it might also be tied to an email address or phone number, which can then be investigated further. Historical analysis is another important step. Even if an account is deleted or renamed, archived web pages, cached search results, or platform-specific history can preserve past activity. This can help establish patterns, such as repeated username changes or linked accounts over time. Finally, the results are compiled and analyzed. The aim is to see how the username fits into the broader digital footprint of the subject. This could mean identifying relationships between accounts, spotting signs of coordinated activity, or discovering connections to real-world identities. The strength of a username OSINT investigation lies in layering these techniques. A single match might be interesting, but when multiple data points line up, the picture becomes clearer — and far more actionable. Best Paid Tools for OSINT Username Investigations Free tools are useful for quick checks, but paid platforms offer deeper coverage, automation, and advanced analysis that professionals depend on. Here are some of the most effective options for username-based OSINT. 1. Lampyre Lampyre is built for both quick lookups and in-depth investigations. Its username search scans a wide range of sources, including
Top Paid OSINT Tools in 2026
Paid OSINT tools help you make sense of the massive amount of public data online. Whether you’re tracking digital threats, running investigations, or verifying identities, these tools offer deeper access, better automation, and professional-grade analysis. This guide covers the best paid OSINT tools in 2026. If you’re serious about intelligence gathering, these tools are worth your attention. What Are OSINT Tools? Open-source intelligence (OSINT) tools help you collect and analyze data from publicly available sources like: Instead of searching each source manually, OSINT platforms automate the work, saving time and boosting accuracy. Why Do You Need OSINT Tools? The internet holds a massive amount of public data. But finding useful intelligence in that data isn’t easy. That’s where OSINT tools come in. They help security teams, investigators, journalists, and businesses find patterns, track threats, and verify information much faster than manual research. Here’s how different professionals use OSINT tools: 1. Security Teams and Cyber Analysts They use OSINT to monitor for early signs of cyberattacks, data leaks, or phishing attempts. For example, threat actors might talk about planned attacks on forums or leak credentials on the dark web. OSINT tools help detect this early. 2. Law Enforcement and Investigators Police and investigators use OSINT to trace digital footprints, monitor online behavior, or verify identities. It’s common to investigate fraud, missing persons, and criminal networks using public digital data. 3. Journalists and Researchers They rely on OSINT tools to collect evidence, verify claims, and uncover hidden relationships between people and organizations. Instead of spending hours searching, OSINT software shows everything in one place. 4. Businesses and Risk Analysts Companies use OSINT to monitor brand mentions, detect fake accounts, assess supply chain risks, and vet partners or customers. It’s also useful in mergers and acquisitions or hiring executive candidates. 5. Financial Services Banks and fintechs use OSINT to investigate money laundering, fraud, and crypto transactions. With the right tool, they can trace wallets, follow transactions, and cross-check leaked data. In short, OSINT tools save time, improve accuracy, and provide context you won’t get from search engines or public databases alone. Why Paid OSINT Tools? Free OSINT tools are useful for one-off searches or learning the basics. But when you need automation, real-time updates, or broader data access, paid tools are often required. Paid platforms offer: Let’s look at the top options available right now. Best Paid OSINT Tools of 2026 If you’re looking for reliable, professional-grade OSINT tools, this list covers the top platforms used by investigators, security teams, and researchers worldwide. These tools offer advanced features like dark web monitoring, relationship mapping, and large-scale automation — all built to handle real investigative workloads. 1. Lampyre Best for: Analysts looking for all-in-one OSINT on people, businesses, crypto, and infrastructureWho it’s for: Law enforcement, banks, investigators, journalists Lampyre is a versatile OSINT platform built for professional investigations. You can analyze phone numbers, IPs, domains, emails, crypto addresses, and social media accounts — all from one interface. You get powerful graph visualizations, table views, and timeline filtering. It works offline or with internet access. Lampyre also supports batch analysis and scripting for automated workflows. Top features: Price: Starts at $5.00 2. Maltego Best for: Network analysis and uncovering connectionsWho it’s for: Cybersecurity teams, government analysts, and fraud investigators Maltego helps visualize relationships between people, companies, domains, emails, and digital assets. It integrates with data providers like Pipl, WhoisXML, and Social Links for enriched intel. Top features: Price: Community edition free; paid plans custom-priced 3. Social Links (Crimewall or SL Pro) Best for: Social media and dark web investigationsWho it’s for: Law enforcement, corporate security, and threat intel teams Social Links offers OSINT tools with access to 500+ data sources across social networks, messaging apps, blockchains, and public records. Crimewall includes graph visualizations, real-time monitoring, and team collaboration features. Top features: Price: Custom enterprise pricing 4. Skopenow Best for: Background checks and identity researchWho it’s for: Insurance firms, security teams, and corporate investigators Skopenow automates person and business investigations using social media, blogs, public records, and news sources. It’s built for commercial teams that need to verify digital footprints quickly. Top features: Price: Custom pricing 5. Babel X (by Babel Street) Best for: Global, multilingual OSINT and geospatial threat detectionWho it’s for: Federal agencies, security teams, and global enterprises Babel X can monitor conversations in over 200 languages across forums, blogs, news, and social media. It uses natural language processing and machine learning to surface relevant signals and threats. Top features: Price: Enterprise-tier pricing 6. DarkOwl Vision Best for: Dark web monitoring and breach discoveryWho it’s for: Cybersecurity firms, threat analysts, and law enforcement DarkOwl indexes darknet sources like Tor, I2P, IRC, and hacking forums. The Vision platform gives access to this archive with search, monitoring, and alerting capabilities. Top features: Price: Custom pricing 7. Paliscope Best for: Digital evidence collection for legal casesWho it’s for: Investigators and law enforcement Paliscope helps collect, organize, and report on digital evidence. It captures metadata, preserves timestamps, and tracks the chain of custody for admissibility in court. Top features: Price: Custom pricing 8. Hunchly Best for: Passive collection of web investigationsWho it’s for: Journalists, researchers, and digital investigators Hunchly runs in the background while you browse and automatically captures every page. It’s used to preserve evidence during online research, especially for data that might be deleted later. Top features: Price: $109 starting price 9. Shodan Enterprise Best for: Finding internet-connected devices and exposed servicesWho it’s for: IT admins, red teams, and infrastructure security professionals Shodan is a search engine for IoT and internet-connected devices. You can find webcams, databases, industrial systems, or any exposed service by scanning the open internet. Top features: Price: custom enterprise pricing Free vs. Paid OSINT Tools: What’s the Difference? Feature Free Tools Paid Tools Data volume Limited High volume, full history Sources Public and basic Advanced (dark web, APIs, private registries) Speed Manual searches Automation + real-time alerts Visualization Basic Graphs, maps, timelines Support Community-only Dedicated support and training Compliance No legal
How to find info about people by phone number or email with Lampyre app tutorial
An email address or phone number can reveal more than you think. With the right tools, these bits of contact info can lead to social media profiles, online accounts, and other public records. This process is part of OSINT (Open-Source Intelligence), which uses public data to find useful information. In this tutorial, you’ll learn how to use the Lampyre app to search for people using just their phone number or email. Lampyre helps you collect and connect this data fast, all in one place. But first, let’s take a look at what email and phone number OSINT is. What Is Email and Phone Number OSINT? Email and phone number OSINT is the process of finding public information linked to an email address or phone number. This type of search is part of OSINT, which stands for Open-Source Intelligence. OSINT means gathering data from public sources like websites, social media, online directories, or search engines. With just a phone number, you can sometimes find a person’s name, social profiles, or business listings. An email address might lead to social media accounts, data breach info, or usernames on forums. These small details can help build a bigger picture of who someone is. Instead of checking each site manually, tools like Lampyre can automate these searches. You enter the email or phone number, and Lampyre looks across many data sources to collect matches and show how they connect. This saves time and helps you spot useful information faster. Getting Started with Lampyre Step 1: Choose Your Mode When you open the Lampyre app, you’ll have two ways to get started. Standard Mode is designed for users who are comfortable with OSINT tools. If you’re new or want a simpler setup, you can pick Simplified Mode instead. In this tutorial, we’ll show you how easy it is to gather information using Lampyre—even if you’ve never used OSINT tools before. First, we’ll go into ‘Quick Start (Simplified Mode)’. You’ll see a blank canvas and a main search bar at the top. That search bar is where we’ll do all our lookups. Step 2: Select Your Search Type In the search bar, you’ll first choose the type of OSINT lookup you want to perform. For this example, select ‘Phone Number’ from the menu on the left. Then, on the right side of the bar, type in the number you want to investigate. Step 3: View Your Search Results With a single search, Lampyre will show you all public data linked to that phone number. For this tutorial, we used a private number to demonstrate what kind of information an average person might have connected to their phone. Because of that, some of the results will be blurred or censored to protect privacy. Step 4: Switch to Table View By default, the results appear as a visual scheme that shows how the data is connected. If you want a more detailed breakdown, you can switch to Table View. Just click the option in the upper left corner. This view gives you more information about each data point in a structured format. Once you select Table View, Lampyre will display a separate tab for each data source related to the phone number. For example, you might see tabs for Amazon, Viber, WhatsApp, and others. Each tab shows detailed information from that specific source. Step 5: Run a Combined Search Now that we’ve covered the basics of a single search, let’s see how to take it a step further. Since the phone number is linked to an email address, we can now run a connected search using both. To do this, go to the ‘Windows’ tab and select ‘List of Requests’ or use the shortcut Ctrl + Y. You can also combine other data types, but for this tutorial, we’ll focus on phone number and email OSINT. Step 6: Enter Your Parameters In this view, you can select all the requests you want to include in the search. If you’re looking for something specific, feel free to filter the list. Otherwise, you can simply select all. Next, on the right side, go to the ‘Parameters’ section. This is where you’ll enter the phone number and email you want to investigate. Step 7: Execute and View Results After entering the data, click ‘Execute’. Lampyre will generate a new connection scheme—this time with much more detail. And just like that, you can uncover a wide range of public information about someone using only their phone number and email address. Final Thoughts As you’ve seen, finding information from a phone number or email doesn’t have to be difficult. With Lampyre’s Simplified Mode, you can run searches, combine data points, and explore connections—all in just a few clicks. Whether you’re doing basic checks or building full profiles, Lampyre helps speed up the OSINT process and makes it easier to follow the trail. Now that you know how it works, try running a few lookups yourself. Start small, stay curious, and build your skills step by step.
OSINT Phone Number Investigations: A Comprehensive Guide
This article was updated and actualized with new data on November 18, 2025. Open-source intelligence (OSINT) techniques can unlock a wealth of information from something as simple as a phone number. Whether you’re an investigator tracing a lead or just curious about a mysterious caller, phone numbers are valuable clues. This guide shows how OSINT helps identify who owns a phone number and what public data links to it. We focus on free tools anyone can use and share best practices for ethical, legal, and effective searches. By the end, you’ll see how a modern OSINT platform like Lampyre can streamline phone number lookups for you. Why Phone Numbers Matter in OSINT A phone number is more than digits—it can reveal someone’s identity and online presence. Many services and social platforms need phone numbers, linking them to profiles, accounts, and personal information. A phone number OSINT search can uncover the owner’s name, location, carrier, and linked social media profiles. In other words, a single number can lead to crucial intel. What You Can Discover In short, phone numbers serve as unique identifiers that cut across both the telecommunication network and the internet. For OSINT investigators, that makes them a key starting point for digging up open-source information about a person or entity. Reverse Phone Lookup: The First Step One of the fundamental techniques in phone OSINT is the reverse phone lookup. This is the process of taking an unknown phone number and searching for information about its owner or origin. In everyday terms, it’s the opposite of looking up someone’s phone number from their name—instead, you have the number and want to find the name (and more). Reverse phone lookup services have been around for a long time. Traditional lookup sites let you enter a phone number to find the subscriber’s name and address. These services aggregate data from phone directories, public records, and user reports. For example, tools like Whitepages or Spy Dialer can disclose information such as the owner’s name, possible addresses, and even the phone company’s name. Similarly, the popular app Truecaller is widely used to identify unknown callers and block spam—it maintains a crowdsourced database of numbers to tell you who might be calling. However, not all reverse phone lookups are created equal. Many free lookup websites rely on static databases that might be outdated. If the number isn’t listed publicly or has changed hands, those services might return little or no information. That’s where OSINT-specific tools up the game: modern OSINT platforms use real-time searches across multiple sources (social media, online profiles, web mentions, etc.) rather than just one database. The goal is to cast a wider net and get up-to-date results. Nonetheless, for an OSINT beginner, starting with a basic reverse lookup can provide quick wins. You might immediately discover the caller is a known business or see that a number has been flagged as a scam in user forums. Let’s look at the variety of free tools and techniques you can use to investigate a phone number. Free OSINT Tools and Techniques for Phone Number Tracing One advantage of OSINT is that many techniques don’t require expensive tools—just creativity and the right websites. Here are some free methods to uncover information from a phone number: Search Engines (Google It) It sounds simple, but entering the phone number into Google (or another search engine) is often the first thing to do. Enclose the number in quotes (e.g., “123-456-7890”) to search for that exact sequence. You might find that the number appears in a business listing, a social media post, or on forums where people discuss unknown callers. Some websites crowdsource reports of spam callers—if the number has been bothering many people, chances are someone posted about it. In OSINT, using general search is a powerful tactic because some sites allow keyword searches by phone number. Always try a web search to see if the number shows up on company contact pages, personal blogs, or data leak repositories. This broad sweep can quickly validate if the number is tied to a known entity or if others have encountered it. Social Media Lookup People often link their phone numbers to social media accounts (for account recovery or friend-finding features). Thus, a phone number can be a handle of sorts to find someone online. Try plugging the number into platforms like Facebook, X (Twitter), Instagram, or LinkedIn search bars. Even if the number itself isn’t visible on a profile, some social networks let you search by phone in certain conditions (for example, Facebook’s search might show a profile if that person hasn’t hidden their phone number from search). Another approach: save the phone number as a contact in your phone and then sync contacts on apps like WhatsApp or Telegram. Often, if that number is registered, you’ll see a profile name or photo in the messaging app. This can give away the person’s name or profile picture, providing leads for further investigation. (Be mindful: some apps might notify the person that you added them, so use a secondary account or a cautious approach for anonymity.) Free Reverse Lookup Websites Besides general search, there are dedicated websites for reverse lookups. Many have free basic searches. For instance, NumLookup is a site that can perform a completely free reverse lookup for phone numbers in the US. Simply enter the number, and it may return the carrier, location, and possibly the name if available. Spy Dialer (mentioned earlier) offers a complimentary lookup for U.S. numbers as well, often giving the name and even a voicemail recording feature. Whitepages provides limited free info like city and phone carrier, with more details behind a paywall. Truecaller’s web version can identify numbers to some extent for free (and their mobile app crowdsources caller IDs). Additionally, community-driven sites like WhoCalledMe, 800notes, or ScamCaller allow users to comment on numbers—these can be gold mines for identifying scam callers or telemarketers by the experiences others shared. While using these, remember that results can vary; a